Creating the Cluster Manager Security Group
- Log into the AWS Console.
- From the AWS Console, go to EC2 and select Security Groups from the NETWORK & SECURITY section of the left sidebar.
- Click Create Security Group.
- Name this security group atc-manager.
- Select your VPC from the VPC drop-down menu.
-
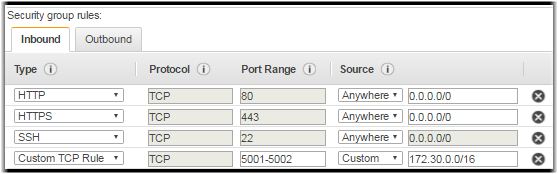
Add the required TCP rules shown in the table below to this security
group.
Click Add Rule and create an inbound rule for each of the ports and protocols listed below to enable connectivity from external systems.
Type Protocol Port Range Source Port Range Description HTTP TCP 80 Anywhere 0.0.0.0/0 External users and systems use this port for browse access to Cluster Manager. HTTPS TCP 443 Anywhere 0.0.0.0/0 External users and systems use this port for browse access to Cluster Manager. SSH TCP 22 Anywhere 0.0.0.0/0 (or your custom IP address) Administrators use this port to SSH into the Cluster Manager. Cluster nodes also use this port to access the cluster-upgrade script. Custom TCP Rule TCP 5001-5002 Custom
VPC subnet of cluster nodes
Launched nodes use this port to retrieve user data from and communicate with the Cluster Manager. Note: The cluster manager runs SSH on port 22 for administrative purposes as well as during the first-boot of the cluster nodes.You must use an SSH key when connecting through this port. For security reasons, Aspera recommends restricting access to port 22 to your own IP address and the subnet used by your transfer nodes.
To do so, configure the SSH TCP rule as follows:
- Set the Source to Custom.
- Set the Port Range to your IP address and the subnet used by your transfer nodes.
- Click Create.