If you need to configure any network proxies or override network speeds, you can do so through the Aspera Connect Network option. Before modifying Connect's network configuration, please review the network requirements, below, which describes ports that may need to be open on your network (e.g. 22, 33001, etc.).
Network Requirements
Your SSH outbound connection may differ based on your organization's unique network settings. Although TCP/22 is the default setting, refer to your IT Department for questions related to which SSH port(s) are open for file transfer. Please also consult your specific Operating System's help documentation for specific instructions on configuring your firewall. If your client host is behind a firewall that does not allow outbound connections, you will need to allow the following:
- Outbound connections for SSH, which is TCP/22 by default, although the server side may run SSH on another port (please check with your IT Department for questions related to which SSH port(s) are open for file transfer).
- Outbound connections for fasp transfers, which is UDP/33001 by default, although the server side may run fasp transfers on one or more other ports (please check with your IT Department for questions related to which port(s) are open for fasp transfers).
Limit Transfer Rates
IMPORTANT NOTE: Unless you need to limit the bandwidth used by Aspera Connect, you should not set any values in these fields.
Launch Aspera Connect () and open Preferences ( ).
You can limit Aspera Connect's transfer rates via the Bandwidth option.
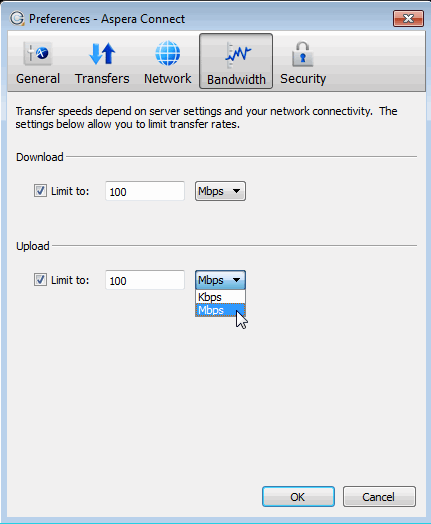
You may limit the download and/or upload transfer rates by enabling the respective checkboxes and inputting a rate in either Mbps or Kbps. Note that your ability to limit these rates depend on the following factors:
- Your network's bandwidth. If your bandwidth doesn't allow you to reach these limits, then they will not be enforced.
- Your Aspera transfer server settings. Settings on your server may prohibit you from reaching transfer rates inputted into these fields.
HTTP Fallback Proxy
The HTTP fallback proxy should only be used for fallback transfers, not for fasp transfers. To set up an HTTP fallback proxy, go to Aspera Connect .
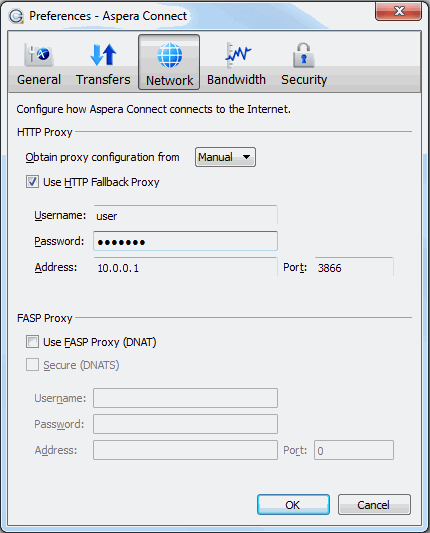
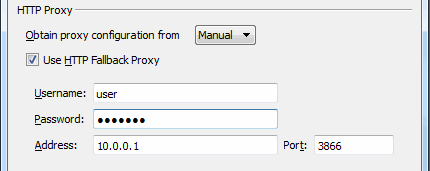
Under the HTTP Proxy section, you can modify the proxy configuration for the server handling HTTP fallback. HTTP fallback serves as a secondary transfer method when the Internet connectivity required for Aspera accelerated transfers (i.e., UDP port 33001, by default) is unavailable. If UDP connectivity is lost or cannot be established, then the transfer will continue over the HTTP protocol based on this proxy configuration.
To configure an HTTP fallback proxy, select one of the following configurations from the drop-down list:
- System: Choose "System" if you want Aspera Connect to use the HTTP fallback proxy settings configured for your Operating System.
- Manual: Choose "Manual" if you would like to manually input your HTTP fallback proxy settings (which may require the assistance of your System Administrator). These settings include NTLM authentication credentials (username and password), as well as the host name/IP address and port number. Please note that the Use HTTP Fallback Proxy checkbox and fields will only be enabled if you select "Manual" from the drop-down list.
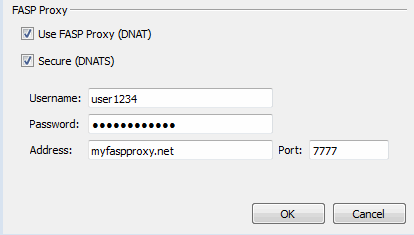
FASP Proxy
When fasp proxy is enabled, Aspera will pass the DNAT or DNATS (secure) username, server address and port to ascp. To set up a fasp proxy, go to Aspera Connect .

To configure a fasp proxy, enable the following checkbox(es):
- Use FASP Proxy (DNAT)
- Secure (DNATS)
Upon selecting the checkbox(es), input your proxy server username, password, address and port number.