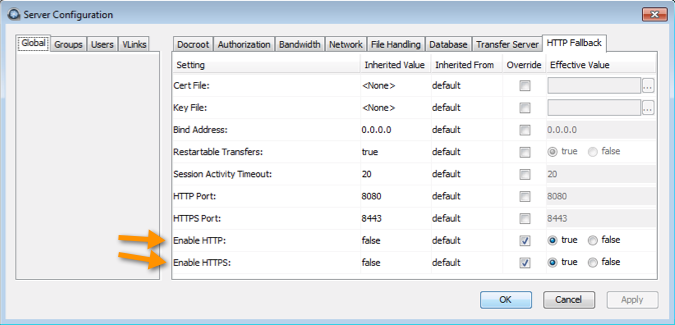
HTTP fallback serves as a secondary transfer method when the Internet connectivity required for Aspera FASP transfers (UDP port 33001, by default) is unavailable. When HTTP fallback is enabled and UDP connectivity is lost or cannot be established, the transfer will continue over the HTTP protocol.
The instructions below describe how to enable and configure HTTP/HTTPS fallback. These instructions assume that you have already configured your Connect Server's Web UI. For additional information on configuring different modes and testing, see the Aspera KB Article "HTTP fallback configuration, testing and troubleshooting."
- Set HTTP/HTTPS to defaults ports (8080 + 8443) and open firewall ports on 8080/8443.
- Set HTTP/HTTPS to standard ports (80 + 443) and open firewall ports on 80/443.
Additionally, the transfer server fallback settings must match the Faspex fallback settings. If the settings don't match, Faspex returns a "Package creation failed" error. Ensure that transfer server has HTTP/HTTPS fallback enabled.