IBM Aspera Faspex supports Security Assertion Markup Language (SAML) 2.0, an XML-based standard that allows secure web domains to exchange user authentication and authorization data. With the SAML model, you can configure Faspex as a SAML online service provider (SP) that contacts a separate online identity provider (IdP) to authenticate users. Authenticated users can then use Faspex to access secure content.
With SAML enabled, Faspex redirects a user to the IdP sign-on URL. The user signs in with the IdP and the IdP sends a SAML assertion back to Faspex, which grants the user access to Faspex. When a SAML user logs in to Faspex for the first time, Faspex automatically creates a new user account based on the information provided by the SAML response. Any changes subsequently made to the account on the DS server are not automatically picked up by Faspex. For more information about user provisioning for SAML users, see User Accounts Provisioned by Just-In-Time (JIT) Provisioning.
IdP Requirements
To use SAML with Faspex, you must already have an identity provider (IdP) that meets the following requirements:
- Supports SAML 2.0
- Able to use an HTTP POST Binding.
- Able to connect to the same directory service that Shares uses.
- Not configured to use pseudonyms.
- Can return assertions to Shares that include the entire contents of the signing certificate.
- If prompted, set to sign the SAML response. (Signing the SAML assertion is optional.)
Configure the SAML IdP
Before configuring SAML in Faspex, make sure you configure your IdP to send a correct SAML response to Shares. For more information, see Configure Your Identity Provider (IdP).For instructions on configuring SAML, see Creating a SAML Configuration in Faspex
SAML and Directory Services
SAML and directory services should not be enabled together. Although there is a directory service behind a SAML IdP, Faspex users do not have access to it. When configuring SAML with Faspex, the following is recommended:- Disable directory service sync.
- Remove existing directory service users from the system.
Multiple SAML Configurations in Faspex
Faspex supports multiple SAML configurations on the same server. Faspex redirects users to the default SAML IdP, but if no default is specified, Faspex directs users to the local login page where users can choose to log into publicly visible SAML configurations or log in locally.In the
following example, East Department and West Department are the names of two SAML
configurations.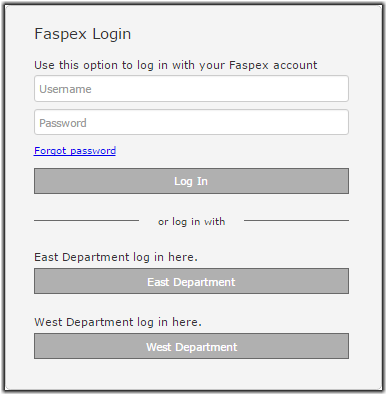
Bypassing the Default SAML IdP
Faspex provides a mechanism for users to bypass the SAML redirect and log in using a local username and password. This feature allows admins to correct server settings, including a mis-configured SAML setup, without logging in through SAML.
To bypass the SAML login, add login?local=true to the end of the login URL. For example:https://198.51.100.48/login?local=true
If users need to access a SAML IdP that is not the default IdP, users can use domain URLs to directly access a SAML configuration. For more information, see Bypassing the SAML Redirect.