Authorization Configuration
The Authorization configuration options include connection permissions, token key, and encryption requirements.
Note: For security, Aspera recommends denying incoming and outgoing transfers
globally, then allowing transfers by individual users, as needed. For a compilation of
server security best practices, see Configuring Shares Security.
- Open the application with root privileges.
- Click Configuration > Authorization.
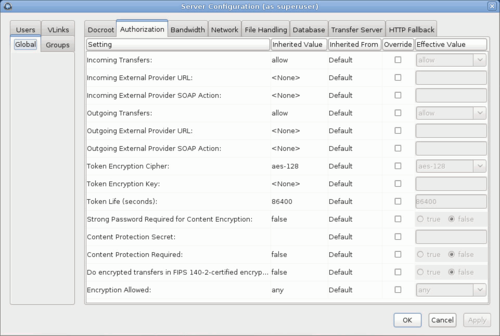
- Edit Global , Groups, and Users settings on their Authorization tabs. Select Override in the option's row to set an effective value. User settings take precedence over group settings, which take precedence over global settings.
Authorization Settings Reference
| Setting | Description | Values | Default |
|---|---|---|---|
| Incoming Transfers | To enable users to transfer to this computer, leave the default setting of allow. Set to deny to prevent transfers to this computer. Set to token to allow only transfers initiated with valid tokens to this computer. Token-based transfers are typically used by web applications such as IBM Aspera Faspex and IBM Aspera Shares and require a Token Encryption Key. | allow, deny, or token | allow |
| Incoming External Provider URL | Set the URL of the external authorization provider for incoming transfers. The default empty setting disables external authorization. Aspera servers can be configured to check with an external authorization provider. This SOAP authorization mechanism can be useful to organizations requiring custom authorization rules. Requires a value for Incoming External Provider SOAP Action. | HTTP URL | blank |
| Incoming External Provider SOAP Action | The SOAP action required by the external authorization provider for incoming transfers. Required if Incoming External Provider URL is set. | text string | blank |
| Outgoing Transfers | To enable users to transfer from this computer, leave the default setting of allow. Set to deny to prevent transfers from this computer. Set to token to allow only transfers initiated with valid tokens from this computer. Token-based transfers are typically used by web applications such as Faspex and require a Token Encryption Key. | allow, deny, or token | allow |
| Outgoing External Provider URL | Set the URL of the external authorization provider for outgoing transfers. The default empty setting disables external authorization. HST Server can be configured to check with an external authorization provider. This SOAP authorization mechanism can be useful to organizations requiring custom authorization rules. Requires a value for Outgoing External Provider Soap Action. | HTTP URL | blank |
| Outgoing External Provider Soap Action | The SOAP action required by the external authorization provider for outgoing transfers. Required if Outgoing External Provider URL is set. | text string | blank |
| Token Encryption Cipher | Set the cipher used to generate encrypted transfer tokens. | aes-128, aes-192, or aes-256 | aes-128 |
| Token Encryption Key | Set the secret text phrase that is used to authorize those transfers configured to require token. Aspera recommends setting a token encryption key of at least 20 random characters. For more information, see Require Token Authorization: Set in the GUI or Require Token Authorization: Set from the Command Line. | text string | blank |
| Token Life (seconds) | Set the token expiration for users of web-based transfer applications. | positive integer | 86400 (24 hrs) |
| Strong Password Required for Content Encryption | Set to true to require that the password for content encryption (client-side encryption at rest) includes at least 6 characters, of which at least 1 is non-alphanumeric, at least 1 is a letter, and at least 1 is a digit. | true or false | false |
| Content Protection Secret | Enable server-side encryption-at-rest (EAR) by setting the passphrase. Files uploaded to the server are encrypted while stored there and are decrypted when they are downloaded. For more information, see Server-Side Encryption at Rest (EAR) or Server-Side Encryption-at-Rest (EAR). | passphrase | (none) |
| Content Protection Required | Set to true to require that uploaded content be encrypted by the client
(enforce client-side encryption-at-rest). For more information, see Client-Side Encryption-at-Rest (EAR). Important:
When a transfer falls back to HTTP or HTTPS, content protection is no
longer supported. If HTTP fallback occurs while downloading,
then–despite entering a passphrase–the file remains encrypted. If HTTP
fallback occurs during upload, then–despite entering a passphrase–the
files are not encrypted. |
true or false | false |
| Do encrypted transfers in FIPS-140-2-certified encryption mode | Set to true for ascp to use a FIPS
140-2-certified encryption module. When enabled, transfer start is delayed
while the FIPS module is verified. When you run ascp in FIPS mode (that is, <fips_enabled> is set to true in aspera.conf), and you use passphrase-protected SSH keys, you must use keys generated by running ssh-keygen in a FIPS-enabled system, or convert existing keys to a FIPS-compatible format using a command such as the following: Important: When set to true, all ciphers and hash
algorithms that are not FIPS compliant will abort
transfers. |
true or false | false |
| Encryption Allowed | Set the transfer encryption allowed by this computer. Aspera strongly recommends that
you require transfer encryption. Aspera
supports three sizes of AES cipher keys (128, 192, and 256 bits) and
supports two encryption modes, cipher feedback mode (CFB) and
Galois/counter mode (GCM). The GCM mode encrypts data faster and
increases transfer speeds compared to the CFB mode, but the server must
support and permit it. Note: To ensure client compatibility when
requiring encryption, use a cipher with the form
aes-XXX, which is supported by all clients and
servers. Requiring GCM causes the server to reject transfers from
clients that are running a version of Ascp 3.8.1 or older. When a client
requests a shorter cipher key than is configured on the server (or in an
access key that authorizes the transfer), the transfer is automatically
upgraded to the server setting. For more information about how the
server and client negotiate the transfer cipher, see the description of
-c in the Ascp Command Reference.Values:
|
any, none, aes-128, aes-192, aes-256,
aes-128-cfb, aes-192-cfb,
aes-256-cfb, aes-128-gcm,
aes-192-gcm, or aes-256-gcm |
any |