Securing Your SSH Server
Keeping your data secure is critically important. Aspera strongly recommends taking additional steps to set up and configure your SSH server to protect against common attacks.
- Changing the TCP port.
- Configuring transfer server authentication.
Aspera also recommends restricting user access to the server, as described in the user setup instructions later in this guide.
Changing and Securing the TCP Port
SSH servers, including the OpenSSH suite included with your product, listen for incoming connections on TCP Port 22 by default. As such, Port 22 is subject to numerous unauthorized login attempts by hackers who attempt to access unsecured servers. An effective deterrent is to close Port 22 and run the service on a seemingly random port above 1024 (and up to 65535).
To standardize the port for use in Aspera transfers, Aspera recommends setting the TCP port to 33001 and closing TCP/22.
Prerequisites:
- Before changing the default port for SSH connections, verify with your network administrators that TCP/33001 is open.
- Before closing port TCP/22, notify users of the change.
Notifying Users - How to Specify TCP/33001
Aspera recognizes that disabling the default SSH connection port (TCP/22) might affect your clients. When you change the port, ensure that you advise your users on how to configure the new port number, from the GUI (if available and used) and from the command line.
- GUI: To change the SSH port in Desktop Client, click
Connections and select the entry for the server
whose ports are changing. On the Connection tab,
click Show Advanced Settings and enter the SSH port
number in the SSH Port (TCP) field.
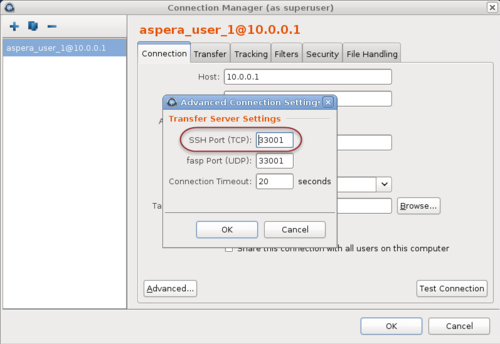
- Command line: Clients running FASP transfers from the command line can specify the port by using the -P 33001 option.
Changing to TCP/33001
The following steps require root privileges.
Configuring Transfer Server Authentication With the Host-Key Fingerprint
To prevent server impersonation and man-in-the-middle (MITM) attacks, Aspera clients can verify the server's authenticity before starting a transfer by comparing the trusted SSH host key fingerprint (obtained directly from the server admin or through an Aspera client web application) with the host key fingerprint returned when the connection is made. In order to do this, the host key fingerprint or path must be set in the server's aspera.conf.